Deliver Better Customer Experiences Everywhere
Turn your customer engagement into a competitive advantage with our simple-yet-powerful cloud contact center platform.




.png)
TEST
Turn your customer engagement into a competitive advantage with our simple-yet-powerful cloud contact center platform.
.png)
Confident Employees
Happy Customers
Many organizations struggle with disjointed systems that spoil the customer experience.
We built our bespoke cloud communications platform from the ground up to enhance the agent process and deliver a perfect customer experience. Every conversation, every channel, everytime.
3 Simple Steps to Launch

Schedule a Demo
See how Platform28 provides a seamless CRX experience.

Run a Customized Trial
Test-drive Platform28 for your own business.

Go Live
Reap the rewards of premium customer service.
A Winning Formula
Combining the right toolset with our experienced Client Success team proves to be a winning formula to delight customers, create happy employees, and increase outcome success.
- Over 20 years experience
- PCI and SOCII Certified
- Technology developed in-house
.png?width=1152&height=648&name=home%20-%20winning%20formula%20(1).png)
Our Clients Speak
Overall, one of the best vendors I've worked with across multiple industries. I highly suggest you give them a close look!

Adam A. Adkins
Service Desk SupervisorUniversity of North Carolina at Asheville
Your leadership and go get em’ attitude has by far exceeded my expectations! Appreciate each of you.
Stephanie Aponte
Director of Governor Kemp's ConstituentService Team at the State of Georgia
If you are trying to solve communication issues, improved efficiency, increase productivity, and cure a telecom technology problem, then Platform 28 is your solution.

Patricia Johnson-Barber
DOAS Contact Center ManagerGeorgia Department of Administrative Services
With Platform28, we now have live dashboards that enable us to easily see in real time, the volume of calls, the number of customers holding, which technicians are currently helping customers, and which technicians are unavailable.

We have been with Platform28 for about 8 years. Their platform gives us the flexibility to do just about anything we can dream up. Other platforms just don't give you that.

Tom Walker
Director of ITStorage Post Self Storage
Amazing Technology
Amazing Engagement
Expertise
Platform28 has been a leading provider of cloud communications for over 20 years.

Flexibility
The ability to make changes faster and easier with our no-code interface.

Open API
Our framework allows integration with any application and system.

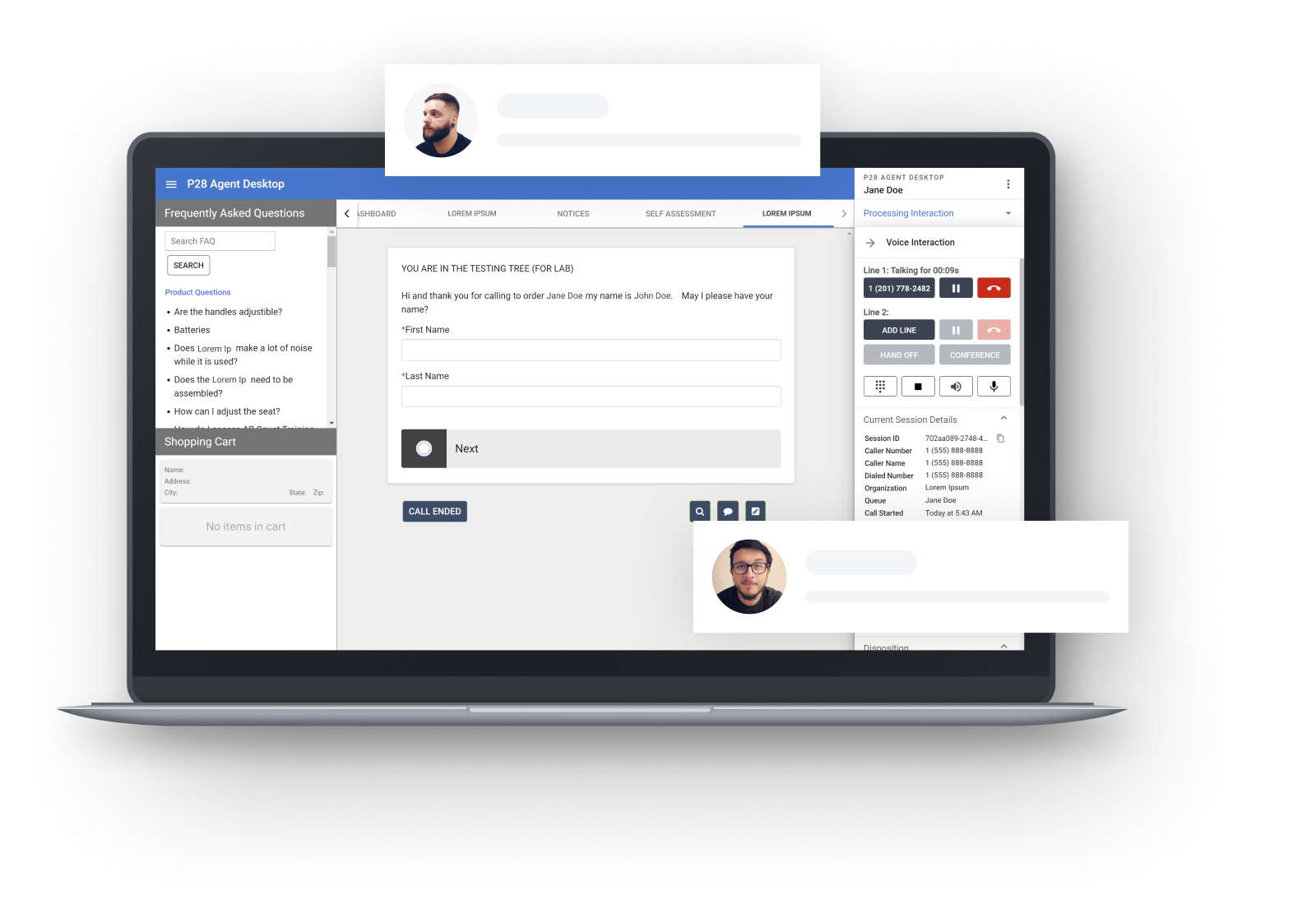
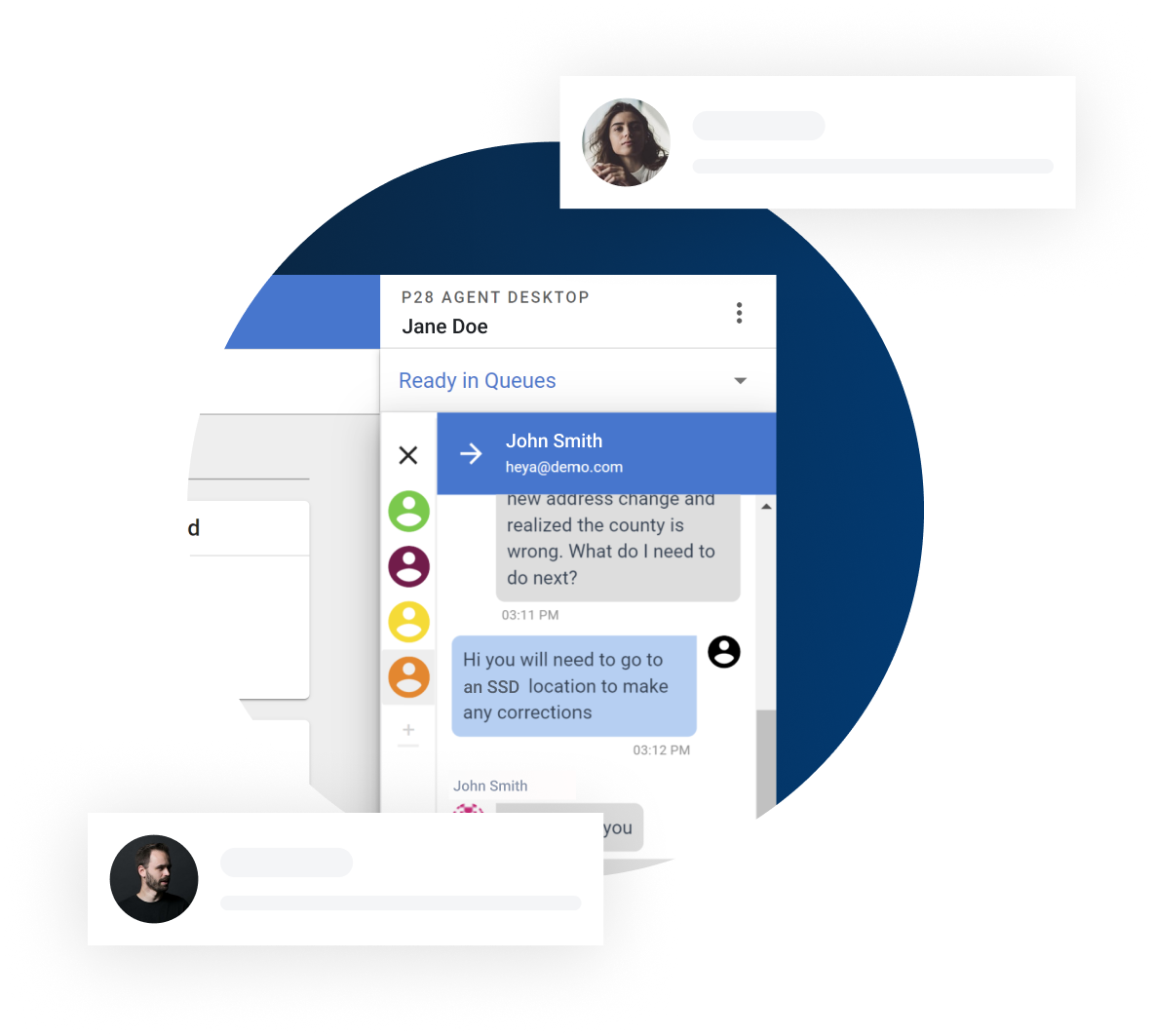
Omni Channel Workspace
A single intuitive interface to handle interactions across all channels.

Unlimited Integrations
Our software is developed with open communication in mind and will integrate with any other software or business tools your company requires.
Latest News & Industry Trends
3 Reasons to Set Up an Omnichannel Contact Center in 2022
The number-one factor for business success is product quality, right?
Wrong.
Here’s a sobering statistic: For a whopping eight out of ten customers...
What Is Intelligent Call Routing, and How Can It Help Your Business?
Contact centers aren’t what they used to be.
In its latest global industry survey, Deloitte notes that contact centers are rapidly evolving into...
From College Kids to Cloud Contact Centers
How it all started...
Mark Ruggles, CEO of Platform28, is a telecommunications specialist focused on creating cloud contact centers that improve...
Technology Built for Human Connection
Today, more than ever, Contact Centers need to focus on providing great customer experiences.
Our technology and expertise make it easy for companies to provide consistent, positive customer experiences. We make it simple to configure seamless customer journeys by combining human, self-service and automated interactions through voice, webchat, email, SMS, and social messaging.
As you create consistent and exceptional customer experiences, your adoption, retention, and productivity rates will soar.
Get Started Today
Now you can focus on what’s really important, growing your business and making your customers happy.